How to intercept (capture, sniff) HTTPS traffic from 3rd party Android apps
Qiuck reference
- HTTP Toolkit for Desktop and for Android
- Bluestacks
- platform-tools (& possible command line tools instead full SDK)
Not working for me:
- Proxifier + Charles Proxy + Bluestacks
- Proxifier + Fiddler + Bluestacks (A SSLv3-compatible ClientHello handshake error - can not resolve this problem )
Extra conditions
- Hardware device OR emulator should be rooted
- 7 version of Android (Nougat) (default for Bluestacks 5). It allow to use user-signed certificate to decrypt https for 3rd party apps
- May be you need to trust http toolkit certificate on desktop by prompt popup
How to root Bluestacks 3,4,5 without BSTweaker
Check root state with "Root Checker" application from Play Market- Press Win + R
- Paste C:\ProgramData\BlueStacks_nxt
- Open bluestacks.conf
- Press Ctrl + F and find all "root" contains lines
- Make it all equal 1
- Restart Bluestacks
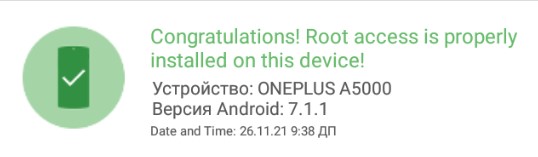
Guide
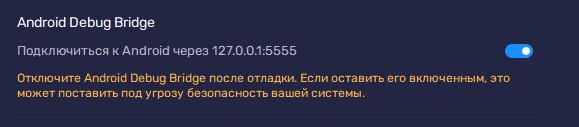
- Enable ADB in Bluestacks extra settings. It give you address & port 127.0.0.1:5555
- Extract platform tools. Open terminal, follow extract pathExecute ./adb connect 127.0.0.1:5555
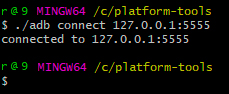
-
- Run app HTTP toolkit on Android
- Open HTTP toolkit on Desktop find option "Android device connected via ADB". It should have active state. Choose it
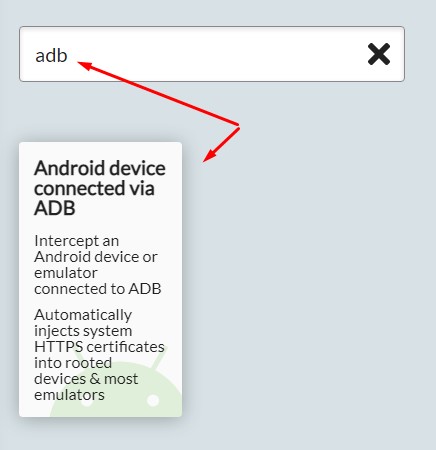
- Select emulator-5554
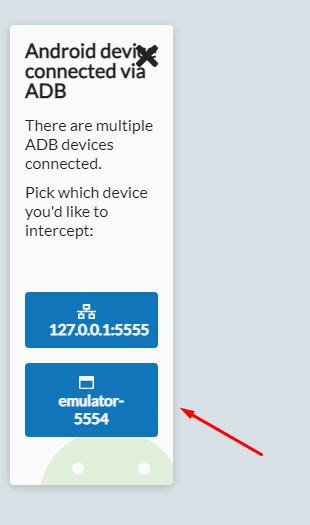
- in Bluestacks in HTTP toolkit app you shuld see success connection

- on Desktop in HTTP toolkit follow view section and you can see decrypted https traffic from all android apps
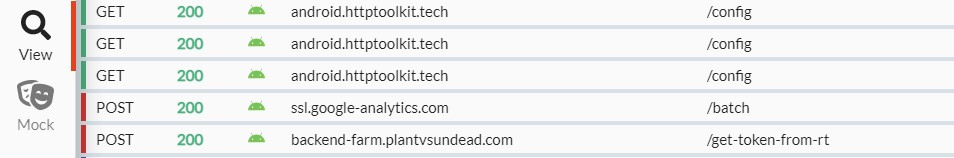
- All is done!